The Impact of Email Security Scanning on Single-Use Sign-On Links
Shifting Cyber Norms: Microsoft security POST-ing to you - Bert Hubert's writings 🔗
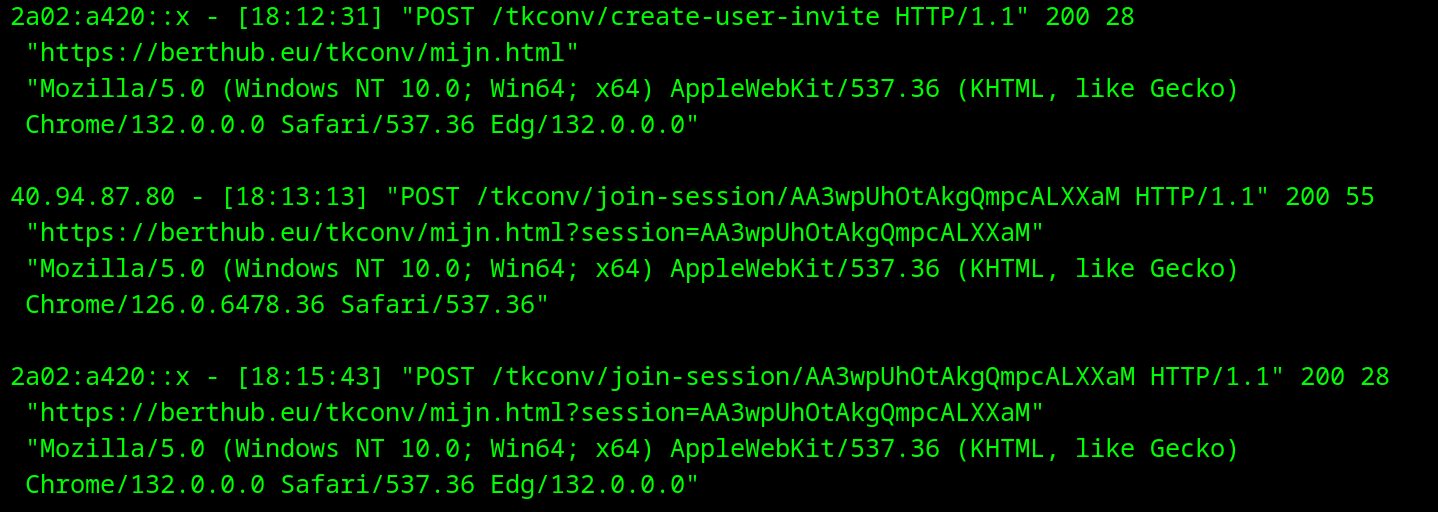
Microsoft and other email security services are increasingly scanning links in emails, executing JavaScript, and sending POST requests, which disrupts single-use sign-on processes. This shift in cyber norms challenges traditional expectations of how GET and POST requests should function, leading to issues where users cannot complete sign-ins because the links are already consumed by security scanners. The author highlights the growing need for developers to adapt their systems to anticipate such behavior and suggests that major tech companies should be more transparent about their practices, especially as they hold significant influence in the digital marketplace.
- Microsoft scans email links and executes JavaScript, leading to unintended POST requests.
- Single-use sign-on links are often rendered useless by these automated processes.
- Developers need to adapt by allowing for multiple uses of sign-on links.
- There is a call for increased transparency from major tech companies regarding their security practices.
What is the main issue with Microsoft scanning email links?
Microsoft's scanning of email links leads to the execution of JavaScript and unintended POST requests, which can consume single-use sign-on links before users can use them.
How should developers respond to these changing cyber norms?
Developers need to modify their systems to allow for multiple uses of sign-on links and prepare for the possibility that security scanners will interact with their links in unexpected ways.
Why is transparency from major tech companies important?
Transparency is crucial because it helps developers and users understand how security practices may affect their services, preventing unexpected disruptions and ensuring accountability from dominant market players.